In an age where smartphones contain sensitive personal and professional information, device security has become a major concern for individuals and businesses alike. From confidential emails and messages to saved passwords and cloud-based documents, a breach of phone privacy can have devastating consequences. This is where security applications like WTMP (Who Touched My Phone?) come in.
WTMP is designed specifically to safeguard smartphones from unauthorized access attempts. By stealthily monitoring unlock actions in the background and capturing intruder selfies, WTMP provides users with an intelligent solution for identifying security risks and deterring potential breaches of privacy.
In this comprehensive review, we’ll explore how WTMP works, its key capabilities, pros and cons, top alternatives, and answer some frequently asked questions about this innovative security app.
What is WTMP?
WTMP, short for “Who Touched My Phone?,” is a smartphone application created by Skylab Apps focused on enhancing device security through improved access control and detailed activity tracking.
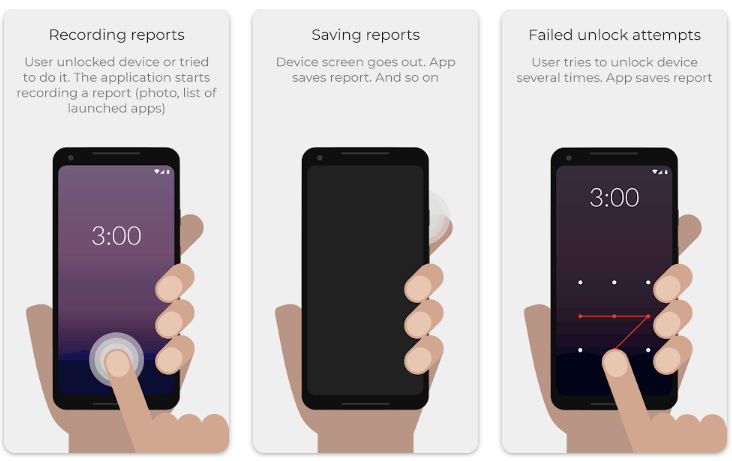
The core functionality of WTMP is to monitor when an individual attempts to unlock your phone without permission and to capture identifying photos using the front-facing camera. This allows users to identify intruders and understand the context of unwanted access attempts on their device.
Along with silently collecting selfies during failed unlocks, WTMP also generates intuitive activity reports showcasing apps opened, screen unlock history, and other potential security risks. With both instant alerts and aggregated reporting, users can gain visibility into threats as they occur while also analyzing trends over time.
How the WTMP App Works
The WTMP app is designed to operate autonomously in the background once enabled, allowing it to provide persistent security without disrupting normal user behavior.
Whenever an incorrect unlock attempt occurs, either via password, PIN, pattern, or fingerprint, WTMP will automatically trigger the selfie camera to capture a photo of the intruder. Depending on user preferences, this image can be stored locally, synced to the cloud, or forwarded to a designated email address or phone number for remote alerts.
Along with real-time unauthorized access notifications, WTMP also tracks application usage, unlock history, and other system-level events that could indicate a security threat. All of this data is available through the app’s reporting dashboard allowing users to identify risks that may have gone unnoticed.
Advanced users can fine-tune security parameters like the number of failed attempts before imaging, customize real-time alerts for specific scenarios, enable stealth mode to reduce visibility of the app itself, and more based on their needs.
Key Features of WTMP
WTMP comes equipped with robust capabilities extending beyond basic intruder selfies and into proactive threat detection and analysis.
Some of the standout features include:
- Real-time intruder alerts: Instant push notifications with images capture during failed unlock attempts.
- Cloud sync & remote access: Seamlessly upload images and reports for access from any internet-connected device.
- Application & event tracking: Logs apps opened, keys pressed, unlock history and other critical system events.
- Customizable alerts: Fine tune notifications for failed logins, unlocked devices, opened apps and more.
- Stealth mode: Prevent WTMP from being visible in the app drawer to obscure its presence.
- Device admin privileges: Critical for enabling deeper system monitoring needed for comprehensive tracking.
- Password protection: Ensure only the owner can access in-app settings and reporting data.
- Media storage controls: Automatically delete older images after a set period to save storage space.
With robust policy configuration, detailed forensic tracking, and cloud integration, WTMP provides a complete 360-degree solution for smartphone security monitoring and threat detection.
Pros of Using WTMP App
| Feature | Benefit |
|---|---|
| Real-time intruder selfies | Identify and deter unauthorized access attempts |
| Customizable alerts | Receive notifications for high-risk events like repeated failed logins |
| Activity & event tracking | Analyze usage trends and system behaviors to identify threats |
| Cloud sync & backups | Access intruder media and detailed reports from any device |
| Stealth mode | Obscure WTMP presence from unauthorized users |
| Remote alerts | Sync images and alerts to other devices for instant notifications |
| Password protection | Ensure only the owner can access sensitive security data |
| Device admin access | Necessary for comprehensive system monitoring and tracking |
Cons of Using WTMP
| Drawback | Details |
|---|---|
| Battery usage | Constant background monitoring does drain battery faster than normal |
| False positives | Motion or extreme light when unlocking may trigger camera incorrectly |
| Limited iOS support | Core functionality only availabe on Android devices currently |
| Privacy concerns | Capturing intruder selfies without consent raises ethical issues |
| Storage usage | Images, videos, detailed tracking logs consume storage over time |
| Learning curve | Numerous settings and alerts require learning to tailor properly |
Top Alternatives to WTMP
| App | Key Features | Price |
|---|---|---|
| Norton App Lock | App locker, web protection, WiFi security, backup | Free or $29.99/year |
| Kaspersky Mobile Antivirus | Real-time protection, app locking, web filtering | Free or $14.95/year |
| Lookout Security | Malware scanning, missing device features, app privacy info | Free or $29.99-$99/year |
| Sophos Intercept X | Business-grade mobile endpoint security | $33.99/user/year |
| Avast Mobile Security | App locking, WiFi security, real-time protection, firewall | Free or $23.99/year |
While alternatives like Norton, Kaspersky, and others provide complementary security capabilities like malware scanning and firewalls, none offer the unique unauthorized access detection and intruder identification capabilities provided by WTMP focused specifically on enhancing smartphone privacy by capturing intruder selfies during breach attempts.
Conclusion and Verdict
For individuals and business owners concerned about smartphone security and protecting sensitive personal information from unauthorized access by intruders, WTMP provides robust, customizable access controls paired with intelligent threat detection.
By instantly capturing photos of anyone attempting to unlock your device using the front-facing camera, WTMP deters intrusions while providing forensic evidence should a breach occur. Backed by detailed app usage tracking, unlock logs, remote backups, and real-time alerts, users gain unparalleled visibility into threats targeting their devices.
While battery life impact, storage usage, and learning curve should be considered, WTMP is currently the most effective solution available specifically focused on smartphone intruder detection and owner privacy protection, making it easy to recommend for security-focused Android users.